These are the steps I used to get the Juniper SRX user firewall feature working with Active Directory. The end result is I can apply firewall policies based on the username of a user or the group of a user.
NOTE: JunOS 17.4R1 or above is required for this feature to work with IPv6
If you do not have any security policies setup that have a match condition for a username/group the user identification service will not start authenticating people; there must first be at least one policy that would require user identification to work.
Active Directory Setup
You should create a user just for the SRX device – do not use an existing account. Juniper KB29659 has some details on the permissions required. The AD user you add requires permissions to read the event viewer logs of the domain controllers as well as access to WMI on hosts to retrieve the current username of the logged in user.
Active Directory User
Create a new user in active directory for the SRX device. The user must be a member of the following groups:
- Distributed COM Users
- Event Log Readers
- Server Operators Make sure that the account has a long password as the account has quite a few permissions assigned. I recommend only using alphanumeric characters with the symbols
_-.to ensure that the password works on the device.
WMI Permissions
WMI permissions need to be added so that the SRX device can query the DC’s and PC’s. It is not recommended, but if the device is a member of the Domain Admins group or the device is a member of the local administrator group on all of your devices the permission will be allowed without further action.
Note that the WMI permissions should be set on ALL devices. If the username cannot be retrieved from the domain controllers alone, WMI will be used to the host itself to try and retrieve the users details.
Manual Method
Open the the WMI Control console by running wmimgmt.msc (eg. start key + r to open run dialog, run that command).
Right click on the “WMI Control (Local)” menu object and click Properties:
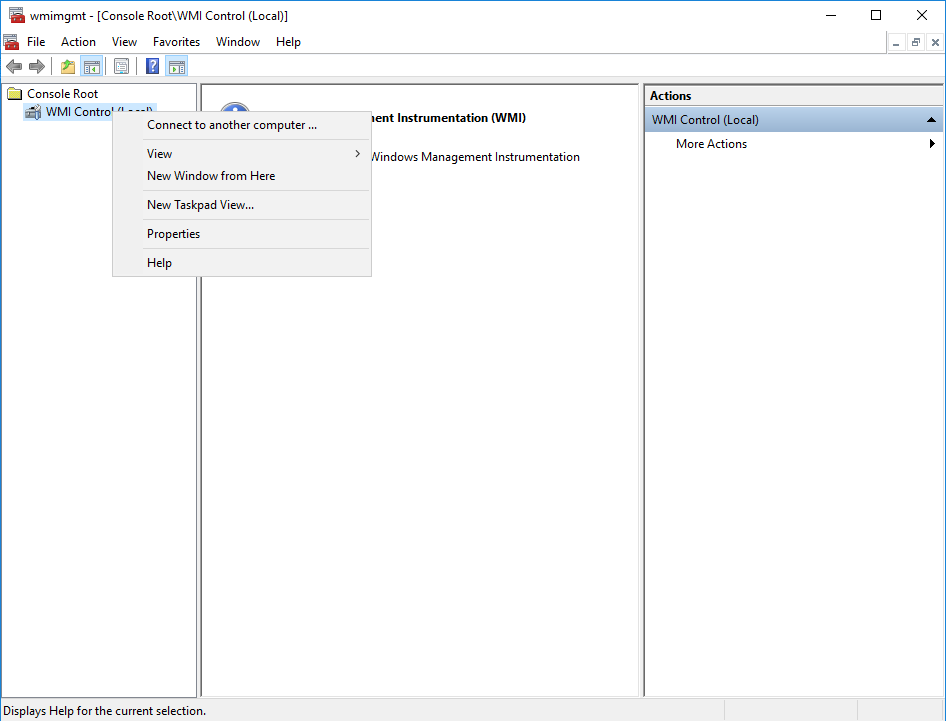
Select the “Security” tab at the top of the properties window and select cimv2:
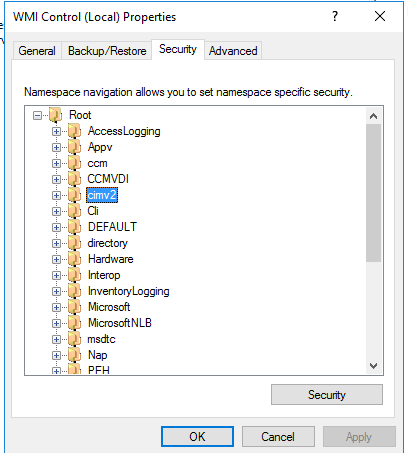
Click on the security button at the bottom to edit the security settings for CIMv2. Click on the add button and add the user that you have created for the SRX device in the previous step. Select these permissions for the user:
- Enable Account: Allow
- Remote Enable: Allow
The permissions window should look like this:
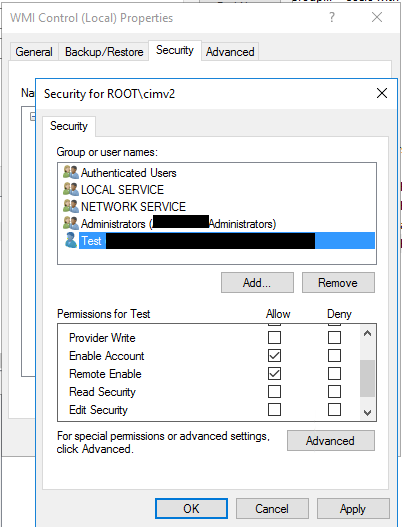
Click OK to apply the settings.
This process must be repeated for all PC’s and domain controllers – you can connect to the remote PC’s via this console.
Group Policy Method
Add the SRX user to the Local Administrators group on each PC. That group has permissions to access CIMv2 via WinRM.
SRX Configuration
There are a twp parts to the SRX configuration:
- LDAP access profile: This is used to retrieve the group membership of users.
- Active Directory settings for the
user-identificationservice: This is used to query the domain controllers and PC’s for the users.
LDAP Access Profile
The LDAP access profile needs to be added to retrieve groups for users. You will need to replace these variables in the below configuration:
- [DOMAIN DN]: This should be the base distinguished name for searches. If your domain is “domain.local” your DN will be
DC=domain,DC=local. - [PASSWORD]: This is the password for the active directory user for the SRX device.
- [USER DN]: This is the username for the active directory user for the SRX device. If your user is in the “Users” OU, the DN for the user will be something like
CN=Juniper SRX,OU=Users,DC=domain,DC=local. - [DOMAIN CONTROLLER]: This is the hostname of a domain controller. If you have more than one domain controller, run this set command with the other domain controller hostnames (for up to 6 other domain controllers total) for redundancy.
set access profile Active-Directory authentication-order ldap set access profile Active-Directory authentication-order password set access profile Active-Directory ldap-options base-distinguished-name [DOMAIN DN] set access profile Active-Directory ldap-options search search-filter sAMAccountName= set access profile Active-Directory ldap-options search admin-search distinguished-name "[USER DN]" set access profile Active-Directory ldap-options search admin-search password [PASSWORD] set access profile Active-Directory ldap-server [DOMAIN CONTROLLER]
The end result should end up looking like this:
{primary:node0}[edit]
root@vsrx# show access profile Active-Directory
authentication-order [ ldap password ];
ldap-options {
base-distinguished-name DC=domain,DC=local;
search {
search-filter sAMAccountName=;
admin-search {
distinguished-name "CN=Juniper SRX,OU=Users,DC=domain,DC=local";
password "$9$..."; ## SECRET-DATA
}
}
}
ldap-server {
dc01.domain.local;
dc02.domain.local;
dc03.domain.local;
}User ID Service
Configure the user ID service to query the domain controllers and PC’s via WMI. You will need to replace these variables in the below configuration:
- [DOMAIN]: This should be the active directory domain name eg.
domain.local. - [SRX USERNAME]: This should be the short format of the SRX username for Active Directory.
- [PASSWORD]: This is the password for the active directory user for the SRX device.
- [DOMAIN DN]: This should be the base distinguished name for searches. If your domain is “domain.local” your DN will be
DC=domain,DC=local. - [DOMAIN CONTROLLER]: This should be the IP address of the domain controller.
set services user-identification active-directory-access domain [DOMAIN] user [SRX USERNAME] set services user-identification active-directory-access domain [DOMAIN] user password [PASSWORD] set services user-identification active-directory-access domain [DOMAIN] domain-controller DC1-IPv4 address [DOMAIN CONTROLLER] set services user-identification active-directory-access domain [DOMAIN] user-group-mapping ldap base [DOMAIN DN] set services user-identification active-directory-access domain [DOMAIN] user-group-mapping ldap address [DOMAIN CONTROLLER] set services user-identification active-directory-access authentication-entry-timeout 30 set services user-identification active-directory-access wmi-timeout 120
You can configure multiple domain-controller statements as well as user-group-mapping ldap address statements, they just need a unique name. The domain-controller statement accepts an IPv4 and IPv6 address where as the ldap address must be IPv4 only. In my situation they are dual stacked so I specify both IPv4 and IPv6 addresses for each domain controller and only the IPv4 address for each ldap address statement.
The finished configuration should look like this:
chris.f@vsrx# show services user-identification
active-directory-access {
domain domain.local {
user {
Juniper-SRX;
password "$9$..."; ## SECRET-DATA
}
domain-controller DC01-IPv4 {
address 192.168.40.200;
}
domain-controller DC01-IPv6 {
address ffff::1;
}
domain-controller DC02-IPv4 {
address 192.168.40.201;
}
domain-controller DC02-IPv6 {
address ffff::2;
}
domain-controller DC03-IPv4 {
address 192.168.40.202;
}
domain-controller DC03-IPv6 {
address ffff::3;
}
user-group-mapping {
ldap {
base DC=domain,DC=local;
address 192.168.40.200;
address 192.168.40.201;
address 192.168.40.202;
}
}
}
authentication-entry-timeout 30;
wmi-timeout 120;
}Security Policies
You can now reference the active directory users and groups in security policies. Here are some sample policies.
To add a policy for all domain authenticated users to send all traffic through the UTM policy named AD-Authenticated you would set a rule like this:
set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM description "Send traffic from all authenticated client IP's through the UTM policy named AD-Authenticated" set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM match source-address any set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM match destination-address any set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM match application any set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM match source-identity "authenticated-user" set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM then permit application-services utm-policy AD-Authenticated set security policies from-zone trust to-zone untrust policy AD-Authenticated_UTM then log session-close
To add a policy for the username “bad-user” on the domain “domain.local” so that all traffic goes through the application firewall named “Block-Facebook-Videos”:
set security policies from-zone trust to-zone untrust policy Bad-User_AppFW description "Send traffic from IP's that belong to the user bad-user through the application firewall policy Block-Facebook-Videos" set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match source-address any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match destination-address any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match application any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match source-identity "domain.local\bad-user" set security policies from-zone trust to-zone untrust policy Bad-User_AppFW then permit application-services application-firewall rule-set Block-Facebook-Videos set security policies from-zone trust to-zone untrust policy Bad-User_AppFW then log session-close
To add a policy for all users in the Active Directory group named “Bad-Users” on the domain “domain.local” so that all traffic goes through the application firewall named “Block-Facebook-Videos”:
set security policies from-zone trust to-zone untrust policy Bad-User_AppFW description "Send traffic from IP's that belong to the user bad-user through the application firewall policy Block-Facebook-Videos" set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match source-address any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match destination-address any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match application any set security policies from-zone trust to-zone untrust policy Bad-User_AppFW match source-identity "domain.local\bad-users" set security policies from-zone trust to-zone untrust policy Bad-User_AppFW then permit application-services application-firewall rule-set Block-Facebook-Videos set security policies from-zone trust to-zone untrust policy Bad-User_AppFW then log session-close
Common Commands
Here are some common commands that help with troubleshooting this feature.
- To show the status of the connections to the domain controllers:
show services user-identification active-directory-access domain-controller status - To show the groups that the Active Directory username “bad-user” is in:
show services user-identification active-directory-access user-group-mapping user bad-user domain domain.local - To show the current authentication table:
show services user-identification authentication-table authentication-source active-directory - To show the current authentication status for an IP:
show services user-identification authentication-table ip-address 192.168.34.231