These steps will get RADIUS authentication working for a Dell switch. After this is configured, you will be able to login to the switch (SSH/HTTP(S)/telnet etc.) using credentials that are validated by your RADIUS server.
Switch Configuration
These configuration settings are all set on the switch.
Generic
These steps should work on most Dell devices but the steps are slightly different for the latest N series firmware release.
- Create the RADIUS configuration on the switch and add a server. In this example, the source IP address for the RADIUS requests is set. This option is NOT required but I do recommend setting it so that in the case of multiple IP’s on the switch you are sure where the requests will be sourced from.
radius-server timeout 3 radius-server source-ip <SWITCH RADIUS REQUEST SOURCE IP> radius-server key <RADIUS PRE-SHARED KEY> radius-server host auth <RADIUS SERVER IP> name "My RADIUS Server" exit
- Create the access list for authentication. In this case the access list “
networkList” will be created which will use both local accounts on the switch and RADIUS authentication. This is recommended so that you can still access the switch using a local account on the switch should the RADIUS server not be reachable.
aaa authentication login "networkList" local radius aaa authentication enable "enableNetList" none aaa authorization exec "Exec_Auth_List" local radius
- Add the RADIUS authentication option to the HTTP/HTTPS server so that if you have the HTTP/HTTPS server enabled on the switch you can use your RADIUS credentials.
ip http authentication local radius ip https authentication local radius
- Test that you can login to the switch with your RADIUS login. I recommend opening a new administrative connection to the switch (don’t log out of your current session) for testing.
- Save the configuration.
N Series (N1500/N2000/N3000/N4000) firmware 6.5+
The latest N series firmware (released Feb 2018) introduced some changes to the RADIUS configuration. These are the settings you will need to use on the newer firmware. On firmware 6.5.1.1 for a new N3048/N3048P stack I have, I ran into issues with RADIUS authentication after configuring it. The only way I could get it to work was reloading the stack after configuring the RADIUS settings. I could not see any reason for this, the logs on the RADIUS server end showed that the authentication was successful but the switch decided to reject the login.
- Create the RADIUS configuration on the switch and add a server. In this example, the source IP address for the RADIUS requests is set. This option is NOT required but I do recommend setting it so that in the case of multiple IP’s on the switch you are sure where the requests will be sourced from.
radius server timeout 3 radius server attribute 8 include-in-access-req radius server source-ip <SWITCH RADIUS REQUEST SOURCE IP> radius server key <RADIUS PRE-SHARED KEY> radius server attribute 31 mac format ietf lower-case radius server auth <RADIUS SERVER IP> primary name "My RADIUS Server" exit
- Create the access list for authentication. In this case the access list “
networkList” will be created which will use both local accounts on the switch and RADIUS authentication. This is recommended so that you can still access the switch using a local account on the switch should the RADIUS server not be reachable.
aaa authentication login "networkList" local radius aaa authentication enable "enableNetList" none aaa authorization exec "Exec_Auth_List" local radius
- Add the RADIUS authentication option to the HTTP/HTTPS server so that if you have the HTTP/HTTPS server enabled on the switch you can use your RADIUS credentials.
ip http authentication local radius ip https authentication local radius
- Test that you can login to the switch with your RADIUS login. I recommend opening a new administrative connection to the switch (don’t log out of your current session) for testing. If you cannot login, I would suggest reloading the switch stack due to the issues I have encountered.
- Save the configuration.
Windows NPS Configuration
To configure a Windows NPS server to answer RADIUS administrative requests from a Dell switch, use these settings for the Network Policy:
Overview
- Type of network access server: Unspecified
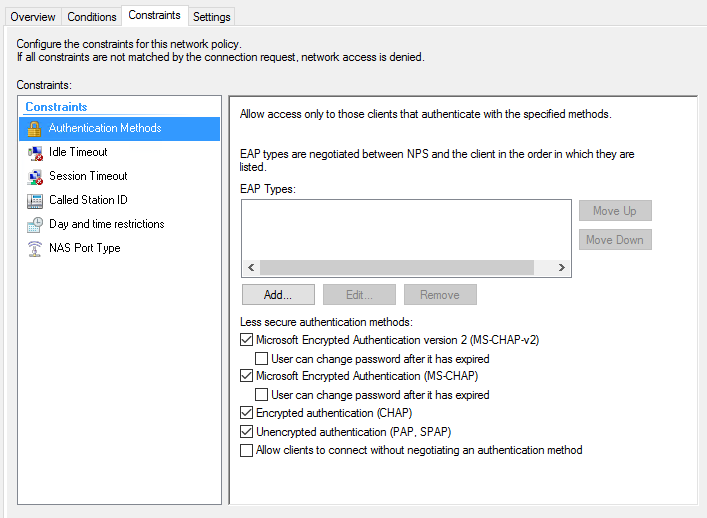
Constraints
Authentication Methods:
- Allow unencrypted login (PAP)
Settings
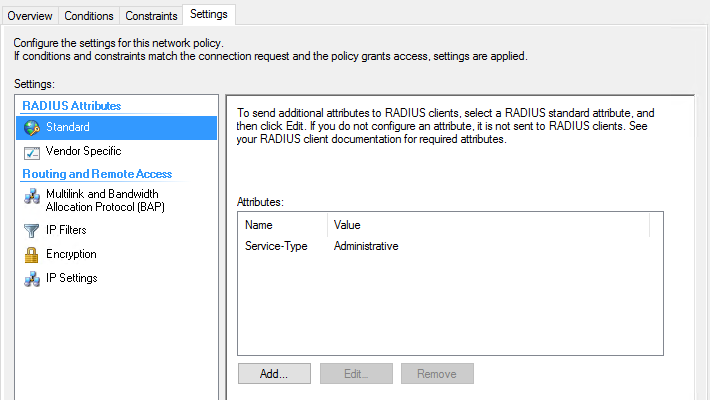
RADIUS Attributes -> Standard
- Click add, select Others bullet point and then select Administrative.
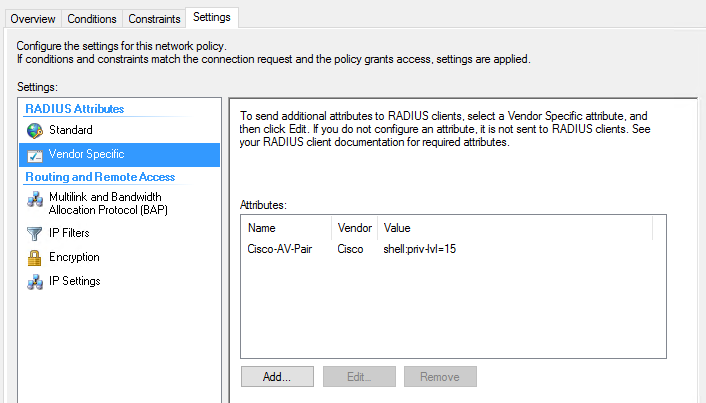
RADIUS Attributes -> Vendor Specific
- Click add, select the Cisco vendor, add an attribute for Cisco-AV-Pair. On the popup window that opens, click add. For the string, enter this:
shell:priv-lvl=15